
Zero Trust: What is it?
Zero Trust is an approach to security that involves implementing multiple layers of controls and security policies to ensure that only authorized users and devices have access to a given resource. It is based on the “never trust, always verify” principle, which means that any access to any type of resource should be treated as untrusted and subject to verification.
This paradigm verifies every device, process, or user that wants to access resources, even if it is a known or authenticated requester.
The Zero Trust Story
This concept was first unveiled by John Kindervag in 2010, when he was vice president and chief analyst at Forrester Research, to designate much stricter enterprise file access control.
Zero Trust considers that trust is a source of vulnerability, in fact granting authorization to each internal or external user to data greatly facilitates access and exfiltration of confidential data.
It took about ten years before this model was again reworked and refined.
Every user is a threat
This model assumes that every user or requester in general can pose a threat, regardless of how many times access has been granted in the past. The CEO of his own start-up who founded his entire business from the same computer, can pose a threat to his business.
Each individual must therefore be authenticated in order to be able to access an application or a file.
Multi-Layer Zero Trust![]()
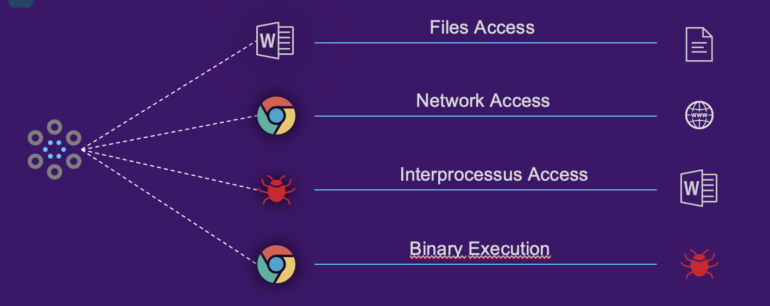
One of the main benefits of a Layered Zero Trust approach is that it helps protect against both external threats, such as hackers and malware, as well as internal threats, such as employees or dishonest contractors. By implementing multiple layers of security controls, organizations can reduce the risk of unauthorized access and limit the potential damage caused by a security breach. The Multi-Layer Zero Trust philosophy was imagined by the R&D teams of Nucleon Security and has been integrated into its EDR (Endpoint Detection and Response) platform.
There are several key components of a multi-layered zero-trust system. These include:
- Identity and Access Management: Ensure that only authorized users and processes have access to network or data resources. This can be achieved through the use of strong authentication methods, such as certificates, and the implementation of access controls to limit the resources that users and devices can access.
- Threat intelligence and analysis: Collecting and analyzing data on potential threats in order to identify and respond to them in a timely manner. This can be achieved through the use of solutions such as XDR (eXtended Detection Response) heterogeneous security event collection and correlation systems coupled with an EDR.
- Continuous Monitoring: Regularly monitor the network and its resources for signs of security threats or vulnerabilities. This can be achieved through the use of security tools such as vulnerability scanners and penetration testing.
By implementing a multi-layered zero-trust approach, organizations can significantly improve their network security and reduce the risk of a security breach. While this approach requires a significant investment in security technologies and processes, it is ultimately worth it for the added protection it provides to the organization and its assets.
Nucleon Security: Endpoint Detection and Response Zero Trust.
Nucleon Security is the first French company to offer Endpoint Detection and Response (EDR) coupled with Zero Trust technology, thus offering enhanced security.
We have been able to adapt this technology to our many media, guaranteeing multi-media comfort to our customers: removable media, cloud storage, shared storage as well as securing internal developments.
Multi layer Zero Trust rules are enforced for any user aiming to access files, networks, internal process but also binary executions, providing unwavering security and control to our customers.
Nucleon Security let’s protect your data together


















