
Cybersecurity challenges in the industrial sector
Cyber security + Ransomware Antoine Botte today26/02/2020 914 1 5

Until today, manufacturers had two different IT work plans. The “classic” computer network, with servers and workstations connected to the Internet; and the production computer network, more isolated with equipment specific to industrial systems, machines rarely connected with the outside and confined to a list of specific tasks.
The evolution of technologies and working methods have led to connecting these two networks. The implementation of increasingly connected management tools and new usages sometimes lead to connecting industrial equipment to the Internet and the cloud.
These new operating architectures automatically bring new cyber risks for the sector. Indeed, these traditionally isolated networks have widened the attack surface for hackers and have brought new types of attacks, with potentially more serious consequences.
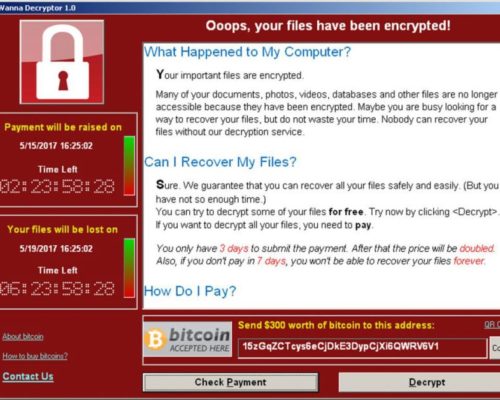
The different types of attacks
In recent years, we have faced significant cyberattacks that uses different technics to reach their objectives. The ransomware-base attacks are the most popular attack, the main objective of these attacks is to encrypt the victim’s data and demand a ransom to recover it.
This was the case for Wannacry in May 2017: the attack affected more than 300,000 machines in more than 150 countries via a vulnerability in Windows system. More recently, in May 2019, the company Picoty SA (specialist in petroleum energy) was asked for a ransom of € 500,000 after being compromised 80% of its data by a ransomware.
the attack affected more than 300,000 machines in more than 150 countries
There is more harmful cyberattacks typology than ransomware-based attacks, it is called Sabotage. Many cyberattacks targeting mostly companies in the industrial sector will simply consist in destructing the production network or security systems. In 2010, the famous Stuxnet attack used a propagation system by USB key to reach a precise target: the industrial systems of a nuclear power plant in Iran. This attack caused a lot of attention because of its complexity, but also because of the clear awareness of the impact that cybercrime can have on our businesses. As mentioned above, you no longer need a USB key to reach an industrial network, you can see it with the NotPetya attack in June 2017 using the same infection method as Wannacry but with a different goal: destroying the data and the system. Many companies were affected by this attack, causing considerable loss of money, particularly for French companies (Saint-Gobain, Auchan, SNCF).
The Trisis (or Triton) attack also made headlines at the end of 2017, it targeted safety machines (SIS) ensuring the safety of people for industrial installations, a deadly program. This attack spread through a vulnerability in software specific to the industrial system used.
Attacks Vectors
Cyberattacks always use at least one flaw to penetrate and infect a machine. There are two main categories of attack vectors.
The best known attack vector is the human fault of course. We often talk about phishing, the system is the same with the aim of abusing user trust by making them click on a malicious link through an email, or by making them open a trapped attachment. Often it is an Office document or a PDF (a false invoice, a confidential press release, etc.). A malicious charge will then be downloaded by the trapped document to break into the machine and start doing its job. The user will of course not be aware of this, unless a message informs him after several minutes that he must pay a ransom to recover his data which has been taken hostage by the malicious program.
The second, lesser-known and more devious attack vector does not require user intervention. This is the exploitation of vulnerability. A vulnerability is a software bug allowing to divert the normal functioning of a program. This vector can sometimes be used directly from the Internet by the attacker, which is where it is most devastating. Without your knowledge and without any interaction with the user, the machine can be a compromise and see the injector of a malicious load. In addition, as we have seen previously, the Internet connection of industrial networks increases the attack surface tenfold. The lack of software updates favors more and more this type of intrusion, this is why it is important to control both its hardware and software as well, in order to guarantee the updating of these to correct known vulnerabilities.
Conclusion
As explained earlier, it is important to educate employees and have the right tools to identify known and new vulnerabilities in order to make the necessary updates.
These recommendations limit the attack surface, but do not make them invulnerable. A malicious employee, an unknown vulnerability or even an exfiltration of data by trusted software remain major threats requiring more advanced security tools. As evidenced by the attacks described, antiviruses confined to the detection of malicious files are now obsolete to deal with these complex threats. It is necessary to turn to new disruptive technologies, more preventive and capable of anticipating abnormal behavior.
Written by: Antoine Botte
Previous post

Cyber security Antoine Botte
Antivirus, EPP and EDR What Differences?
Similar posts


Don’t miss our insights
-
Recent Posts
Categories
Search in the site
Most popular
Corona-Malware the New Trend to Steal Your Data

Rollback and Remediation against Hakbit Ransomware

What is Threat Hunting and how it can benefit your organisation?

How Maze abuse legitimate installer to trick your defense?

What are Machine Learning and Multi-Layer Zero-Trust and why use them in an EDR ?

Copyright 2023 Nucleon Security








