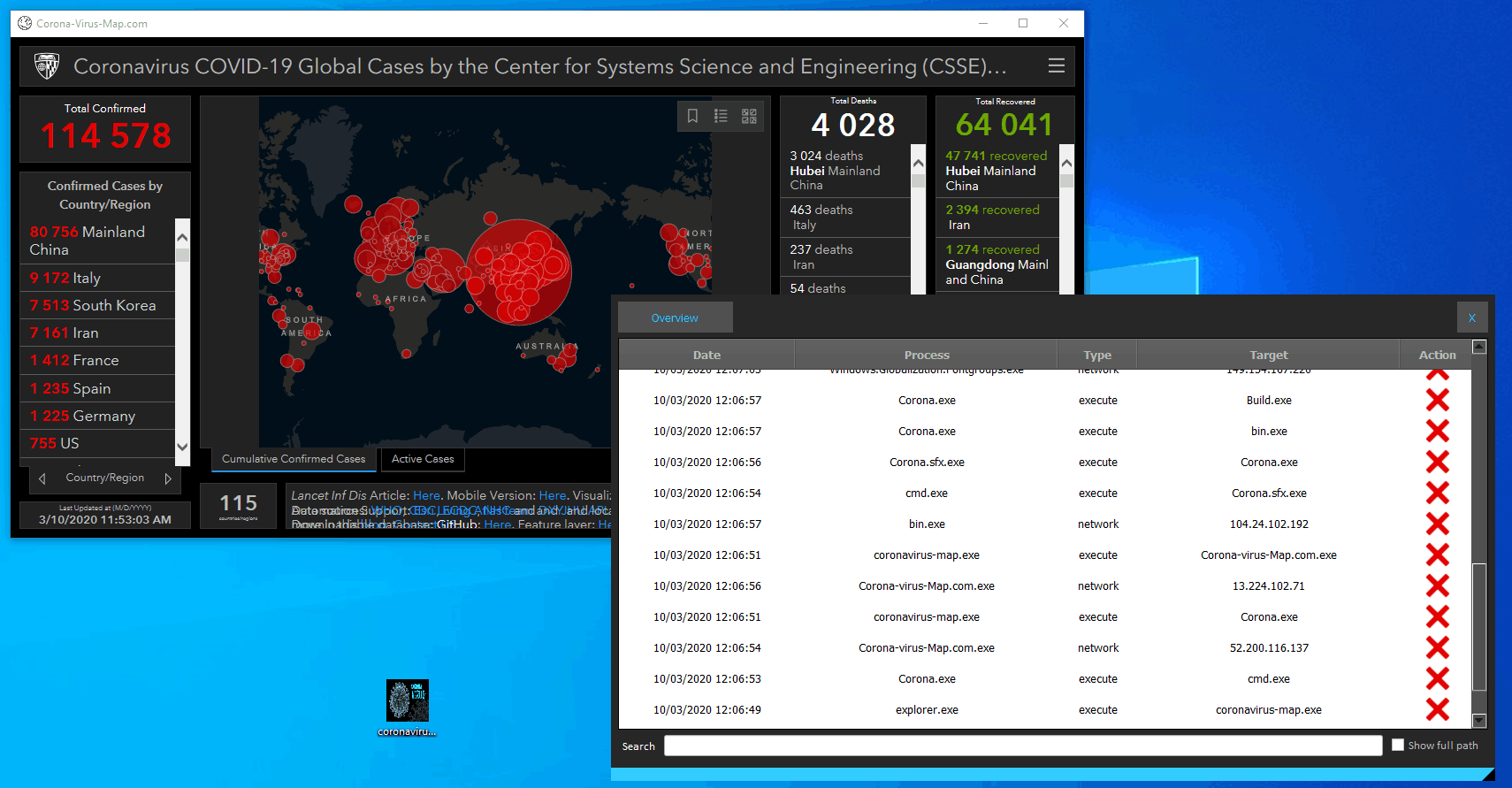
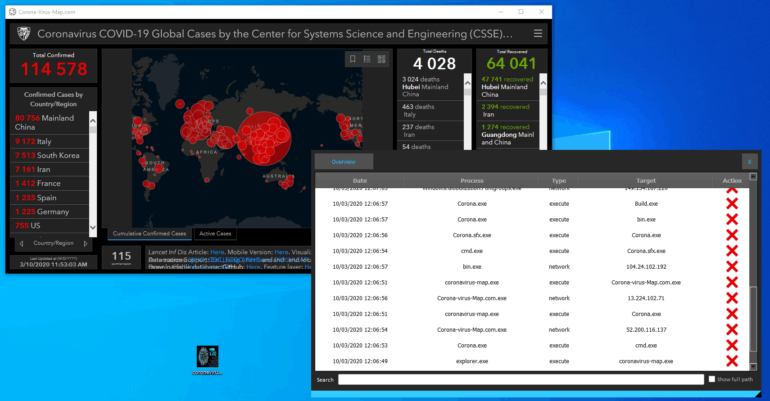
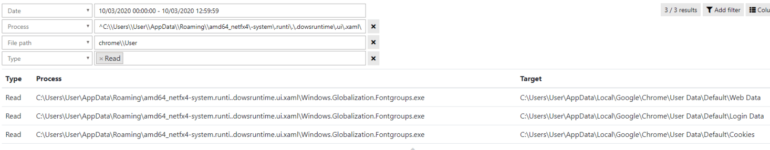
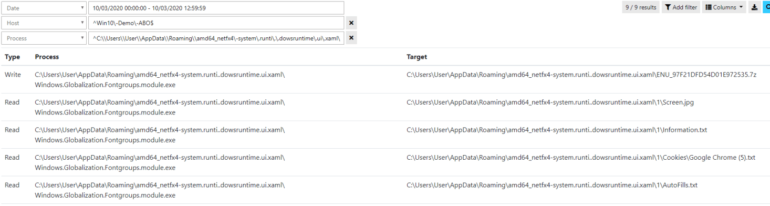
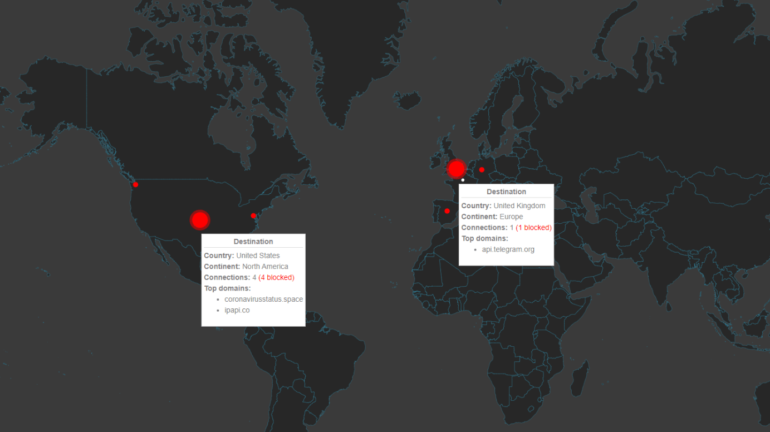
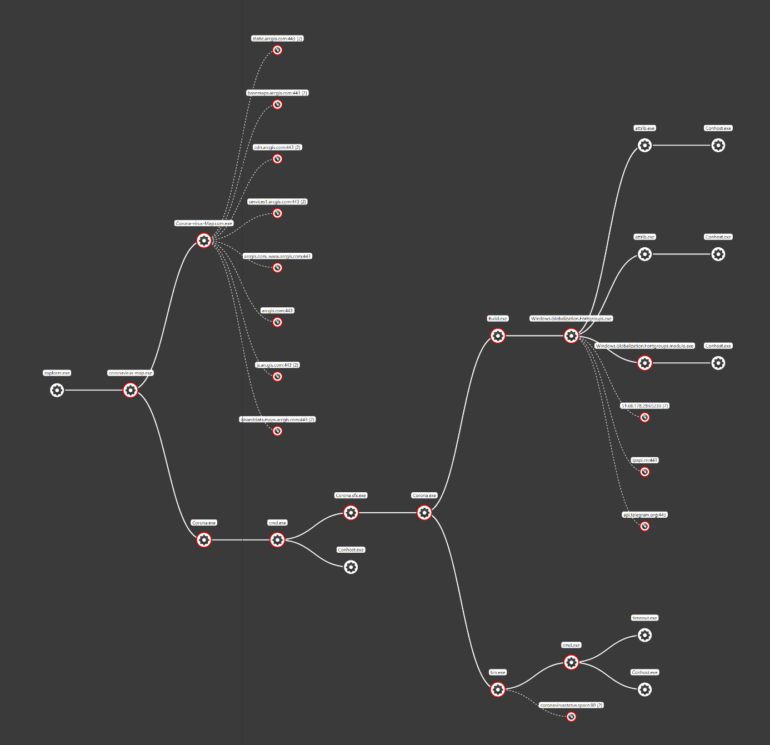
This new malware (Corona-virus-Map.exe) masquerades as an application for monitoring cases of Coronavirus infections. This program is apparently a software allowing to visualize the infection map of Coronavirus, it is based on the official map ( https://gisanddata.maps.arcgis.com/apps/opsdashboard/index.html#/ bda7594740fd40299423467b48e9ecf6 ) by integrating browser viewing functionality as seen in the screenshot.