What is Venus Ransomware?
Venus is a ransomware discovered by a malware researcher called S!Ri. Its primary function is file and system encryption, all affected files are modified with a .venus extension as shown in the figure below. After encrypting all the data, the desktop wallpaper is replaced with a note asking the victims to pay to decrypt their data

How does it infect hosts?
The Venus ransomware appears to target publicly available Remote Desktop Services which are based on Remote Desktop Protocol(RDP), regardless of those running on no standard TCP ports.
How does this ransomware behave ?
One executed on the target machine, Venus ransomware will attempt to terminate all the processes ( as shown below ) associated mostly with database servers and Microsoft Office applications.

The ransomware also clears event logs, shadow copies, and disables DEP (Data Execution Prevention) using the following command :

and when the encryption is done an HTA (HTML Application) ransom note will automatically appear as shown below

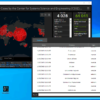
While executing Venus Ransomware, the Nucleon EDR captured network activities as shown below, and it appears that the ransomware is sending data to the local addresses via port 9

More information about the use of port 9

The Venus ransomware is still active, with fresh submissions being published to ID Ransomware on a daily basis.
The Venus ransomware has been detected by the Nucleon EDR see the demo here