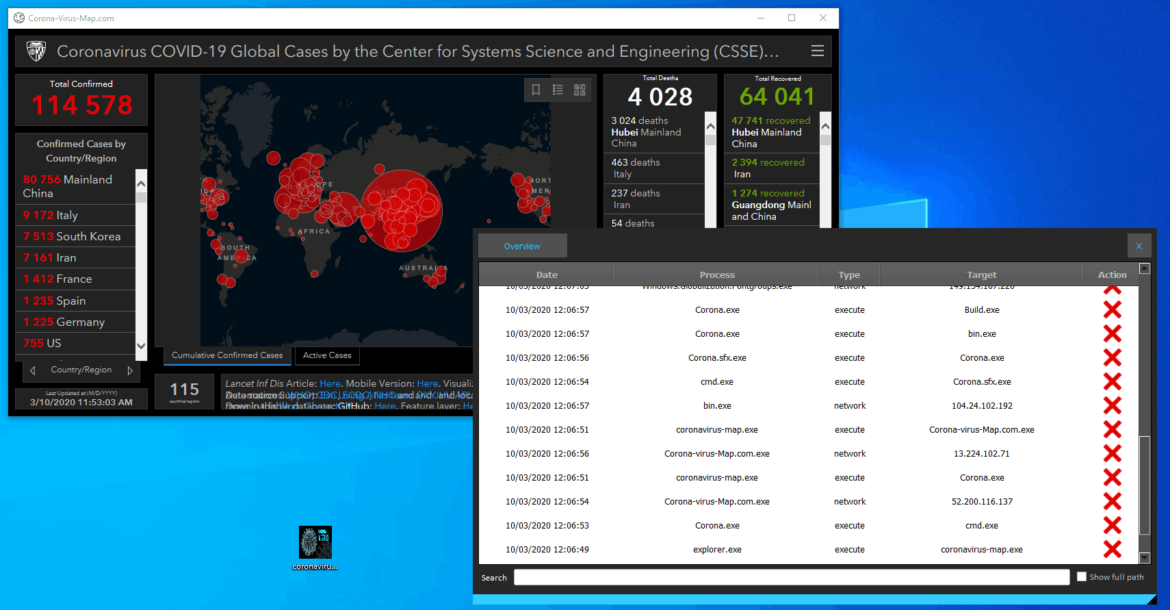
How Maze abuse legitimate installer to trick your defense?
Malware developers are always looking for new technics to bypass security systems. In this article we will see how Windows Installer can be abused to deliver malicious code, and how the famous ransomware Maze uses this type of technic. Create malicious MSI files An MSI file is a compressed database [...]