Cyberattacks always use at least one flaw to penetrate and infect a machine. There are two main categories of attack vectors.
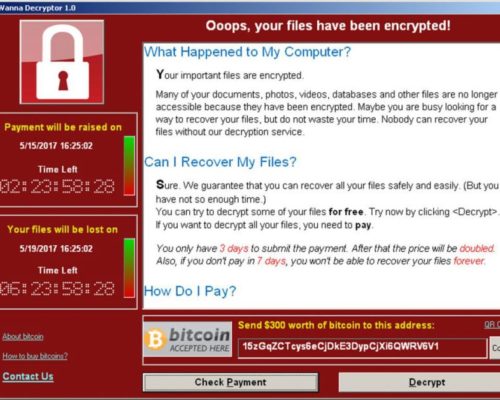
The best known attack vector is the human fault of course. We often talk about phishing, the system is the same with the aim of abusing user trust by making them click on a malicious link through an email, or by making them open a trapped attachment. Often it is an Office document or a PDF (a false invoice, a confidential press release, etc.). A malicious charge will then be downloaded by the trapped document to break into the machine and start doing its job. The user will of course not be aware of this, unless a message informs him after several minutes that he must pay a ransom to recover his data which has been taken hostage by the malicious program.
The second, lesser-known and more devious attack vector does not require user intervention. This is the exploitation of vulnerability. A vulnerability is a software bug allowing to divert the normal functioning of a program. This vector can sometimes be used directly from the Internet by the attacker, which is where it is most devastating. Without your knowledge and without any interaction with the user, the machine can be a compromise and see the injector of a malicious load. In addition, as we have seen previously, the Internet connection of industrial networks increases the attack surface tenfold. The lack of software updates favors more and more this type of intrusion, this is why it is important to control both its hardware and software as well, in order to guarantee the updating of these to correct known vulnerabilities.
As explained earlier, it is important to educate employees and have the right tools to identify known and new vulnerabilities in order to make the necessary updates.
These recommendations limit the attack surface, but do not make them invulnerable. A malicious employee, an unknown vulnerability or even an exfiltration of data by trusted software remain major threats requiring more advanced security tools. As evidenced by the attacks described, antiviruses confined to the detection of malicious files are now obsolete to deal with these complex threats. It is necessary to turn to new disruptive technologies, more preventive and capable of anticipating abnormal behavior.