What is Threat Hunting and how it can benefit your organisation?
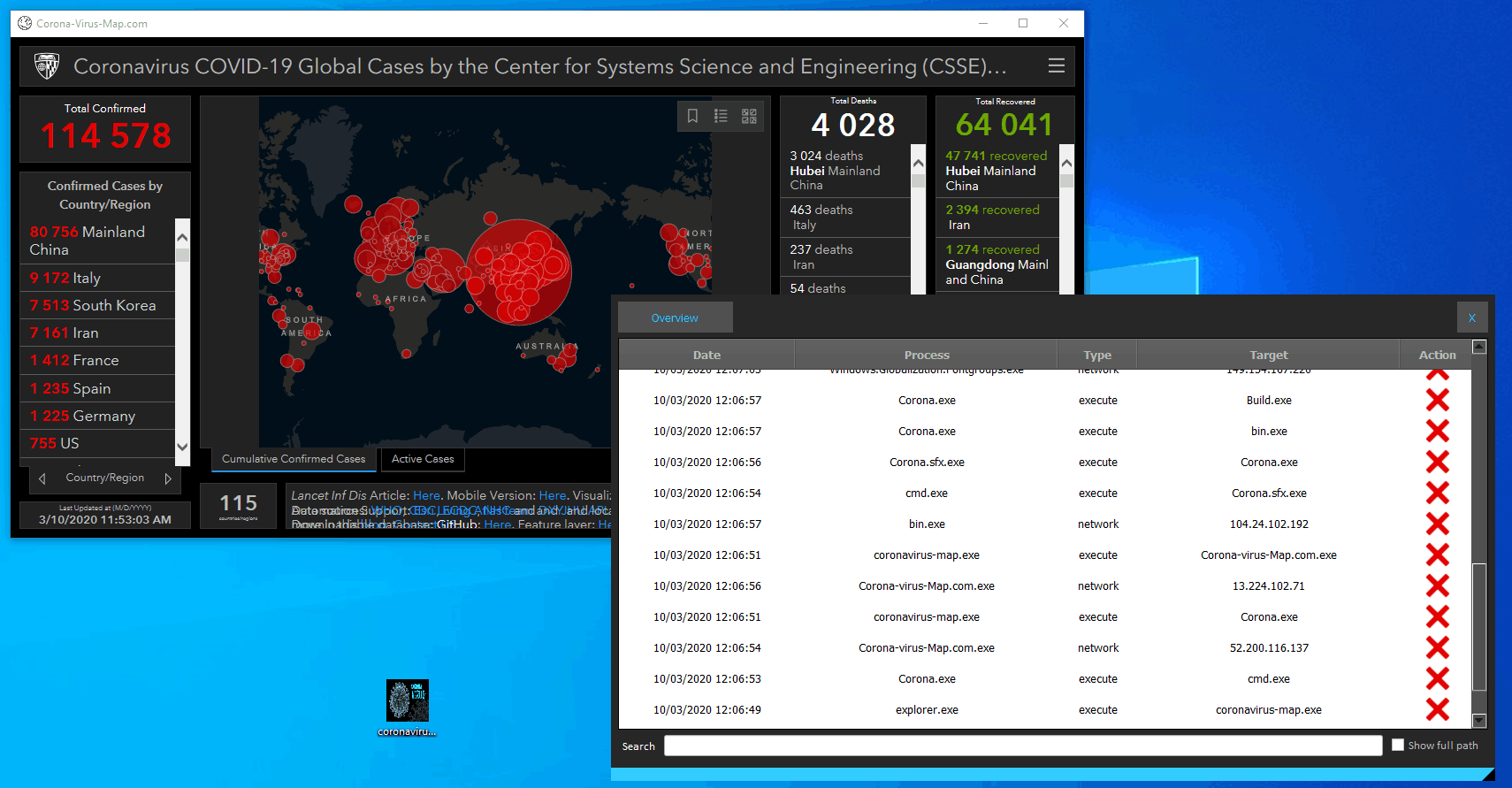
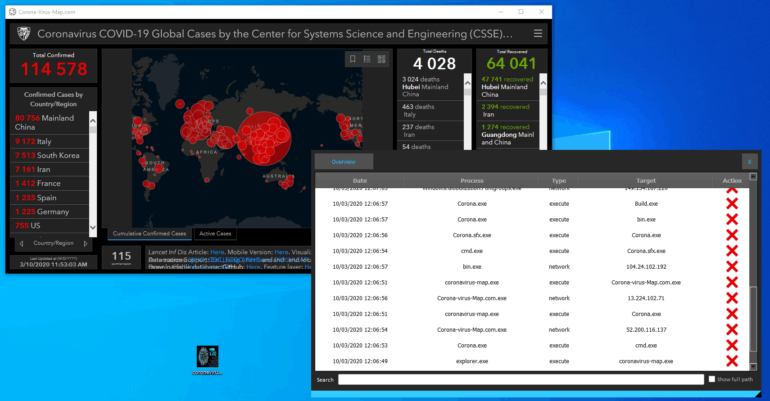
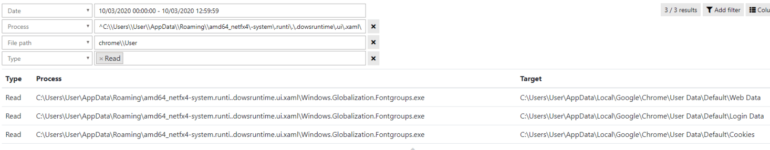
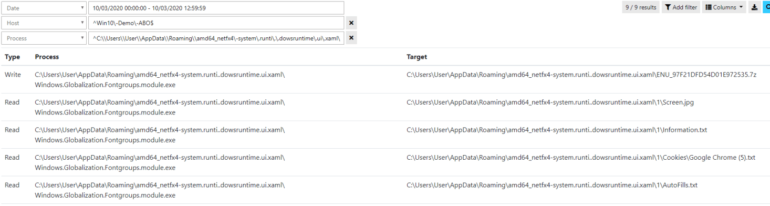
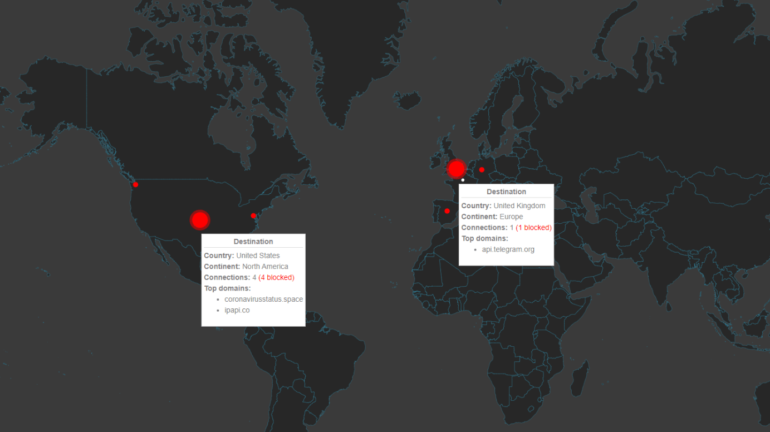
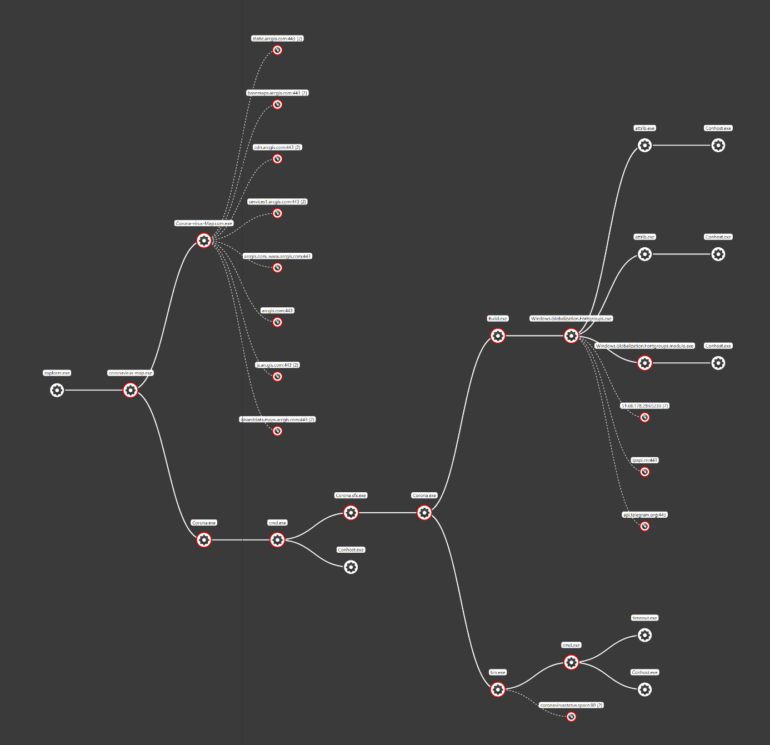
What is threat hunting and why we need it now ? Threat hunting designates all the activities conducted by a threat hunter or a cyberthreat analyst in order to find hidden persistent threats inside an organization’s infrastructure. Abnormal events such as a connection to an unknown server, access to a sensitive process memory or a DLL injection are some examples of what a [...]