
How Maze abuse legitimate installer to trick your defense?
Cybersécurité + Ransomware + Malware Antoine Botte aujourd'hui16/09/2020 1754 2 5

Malware developers are always looking for new technics to bypass security systems. In this article we will see how Windows Installer can be abused to deliver malicious code, and how the famous ransomware Maze uses this type of technic.
Create malicious MSI files
An MSI file is a compressed database that contains files and commands to execute in addition of many metadata in order to ensure the version management of the deployed program.
Using MSI files to trigger an attack can be an easy way to bypass analysis engine. Like a packer, the content will be hidden in a new file that is apparently clean.
Any install builder can be used to embedded and deploy an exe file. Some tools are also available to convert an exe to an MSI file in no time.
The Metasploit framework also provide a MSI output file when creating a payload, it uses the same embedding technic.
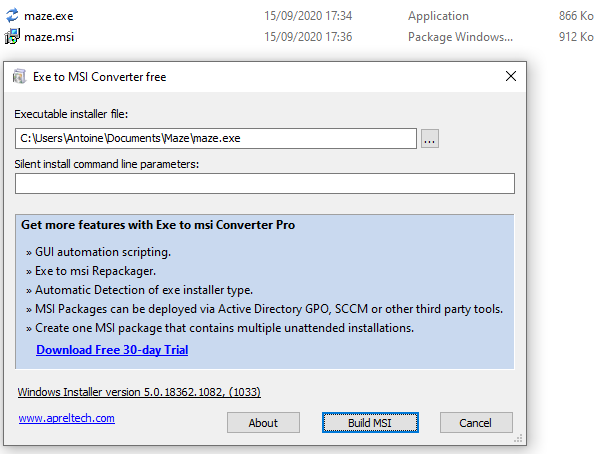
In this example the exe file is just stored in the MSI like an archive, the original file can be recovered simply by unzipping it using 7-Zip for example:
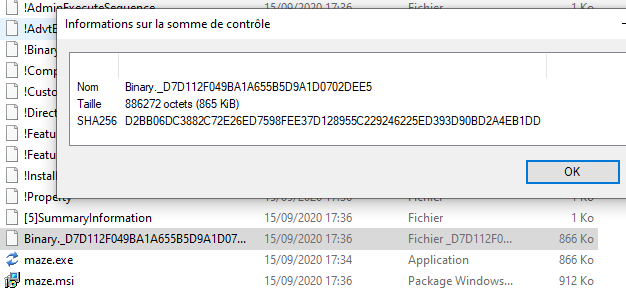
By submitting the original Maze payload (exe) to VirusTotal, we can see that the detection rate is 59/68.
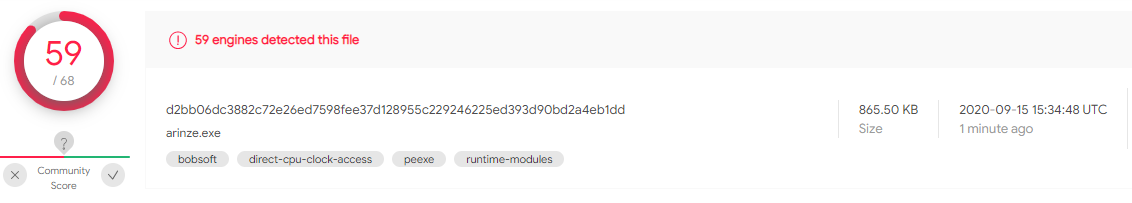
On the other hand, the detection rate drops to 32 for the MSI version. This is still high, but this show how security product can be weak in detecting hidden payload in MSI files.
Abuse Msiexec command
The technic shown before is a lazy technic, that can also be associated to the direct download feature of Msiexec. In fact, the /i option can retrieve and load an MSI file remotely, this is frequently used to deploy a malicious installer payload.
But Msiexec also provide some fishy features that can be used by attackers to deploy malicious payload, for example, the option /y or /z allows to load any DLL. This will call the function DllRegisterServer or DllUnRegisterServer of the DLL directly from Msiexec. No MSI file is required, only a DLL, like an alternative to start rundll32 to load a malicious library.
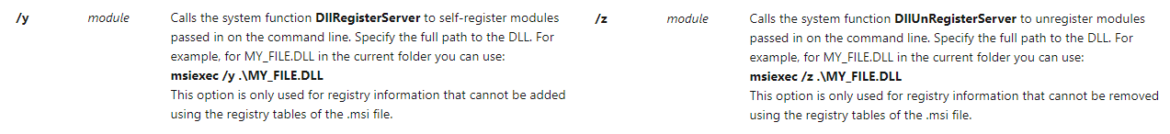
This DLL registration process is provided by regsrv32 tool, which is also used in many Applocker bypass procedures, these methods are also available in the Metasploit framework.
According to Microsoft, the goal of this DLL registering feature is to provide a fast way to deploy new software:
A real MSI Maze case
The last seen versions of maze embedded in a MSI file are even more sophisticated.
Even if maze is a well-known ransomware for security professionals, the payload we are talking about still has a poor detection rate, why?
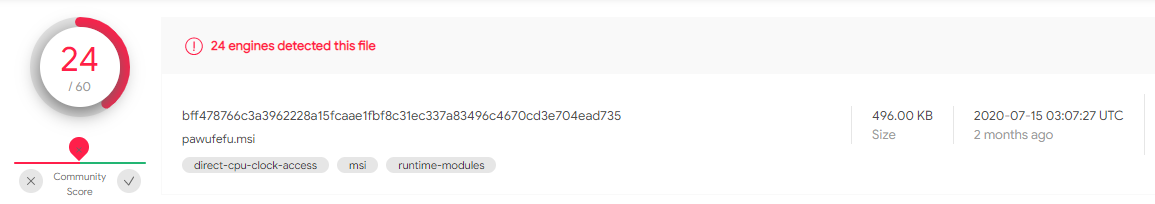
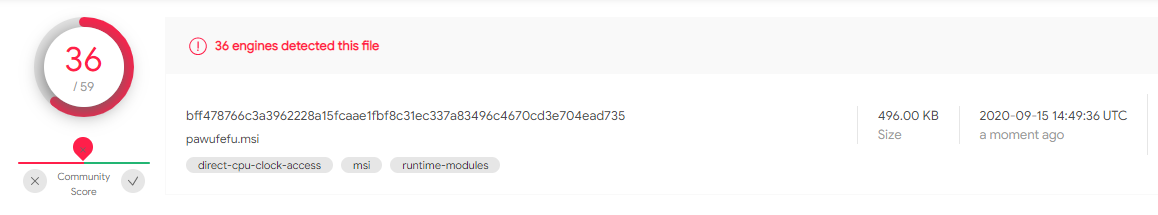
The payload is a real and valid MSI file, but this time the sample has an extremely poor content when extracted like a classical archive:
An MSI inspector tool is required to understand the behavior of this package.
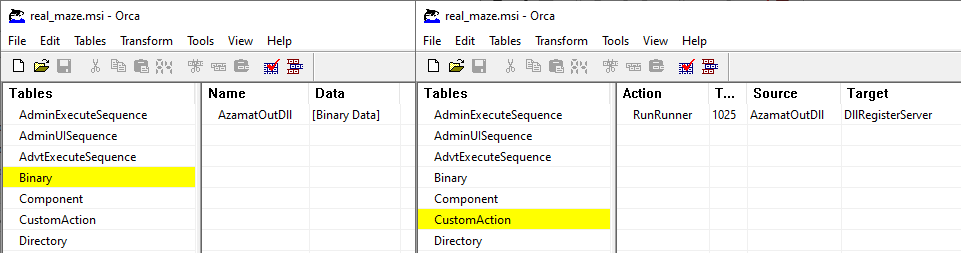
As we can see here, there is in fact a binary payload stored as “AzamatOutDll”. This binary payload is started by Msiexec by calling the DllRegisterServer like the /y options of msiexec.
Unlike other MSI technics we saw that always need a malicious payload dropped on the disk, this installer file is able to load the malicious content itself by calling the DLL entrypoint DllRegisterServer.
This makes the detection even harder for security product because the payload is hidden in the MSI, and results in a legit signed process (msiexec.exe) executing malicious code without performing any process injection to hide its activity.
This MSI loading technic was previously used in Ragnar locker which is now in partnership with Maze to ensure a better data leak management.
Maze VS Nucleon-Smart-Endpoint
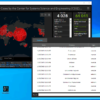
The analysis engine of Nucleon EDR platform is powered by a Machine-Learning model which is able to understand MSI file in all of their forms.
Thanks to this, the MSI layer is fully transparent for the detection engine which always ensure a good detection rate against this type of threat:
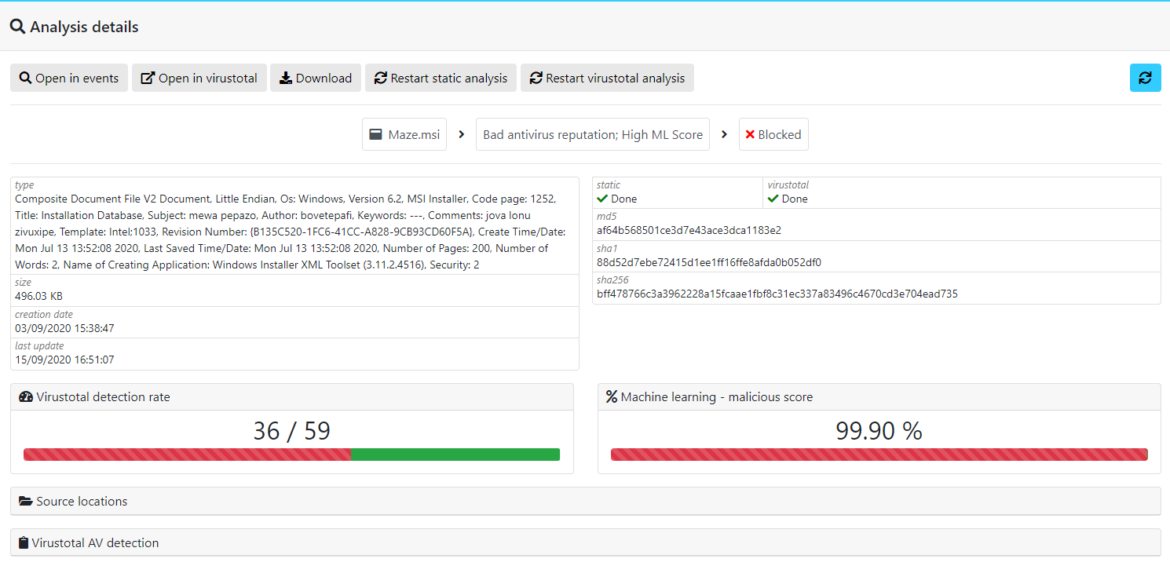
In addition to the analysis engine and the Multi-Layer Zero-Trust protection rules, Nucleon-Smart-Endpoint provides a rollback and remediation features to face ransomware attacks and restore your data after an attack.
Here is a quick demo of this MSI maze payload against Nucleon-Smart-Endpoint EDR. The endpoint is set to detection mode to allow the malware to execute and access the data, otherwise it would be blocked, and maze would not be executed thanks to the analysis engine.
Written by: Antoine Botte
Previous post

Cybersécurité Nucleon Security
What is Threat Hunting and how it can benefit your organisation?
What is threat hunting and why we need it now ? Threat hunting designates all the activities conducted by a threat hunter or a cyberthreat analyst in order to find hidden persistent threats inside an organization’s infrastructure. Abnormal events such as a connection ...
Similar posts


Don’t miss our insights
-
Articles récents
- Quels sont les enjeux stratégiques de la souveraineté en matière de cybersécurité ?
- Qu'est-ce que le Zero-Trust multicouche et comment il peut aider votre organisation
- Nucleon Security Vs Venus Ransomware
- Nucleon Security présenté comme l'une des meilleures solutions EDR
- Avez-vous besoin d’un EDR ? les 10 question à se poser.
Catégories
Search in the site
Most popular
Corona-Malware la nouvelle tendance pour voler vos données

Rollback and Remediation against Hakbit Ransomware

What is Threat Hunting and how it can benefit your organisation?

How Maze abuse legitimate installer to trick your defense?

Qu’est-ce que le Machine Learning et le Multi-Layer Zero-Trust et pourquoi les utiliser dans un EDR ?

Copyright 2023 Nucleon Security








