Plus lus

Last Insights

superviser
Répondre
Rollback and Remediation against Hakbit Ransomware
Cybersécurité + Ransomware + Nucleon Security News Antoine Botte aujourd'hui11/06/2020 1619 3 5
Ransomwares are still the most widespread cyberattacks targeting corporate data. That’s why in addition of the Multi-Layer Zero-Trust implementation in Nucleon Smart Endpoint EDR, we now release new post-exploitation features. In this article we will demonstrate our rollback and remediation features against Hakbit ransomware.
The goal is to reduce the gap between the first action of an attack, and the back to normal situation. This is applicable to ransomwares attack, but also destroyer malware, or malicious use on the network that would simply delete all the data on a storage.
The key to provide an effective rollback system is to retrieve all the activity history of each endpoint of the IT Infrastructure, plus a snapshot system to request the data as to be restored.
The « deep logging » features provided by Nucleon Smart Endpoint EDR allow to monitor all the network and system activity of processes constantly. In addition to this feature, the security policy now include the rollback configuration panel in order to choose how to snapshot the data of the endpoints to restore them after an incident.
Simple configuration
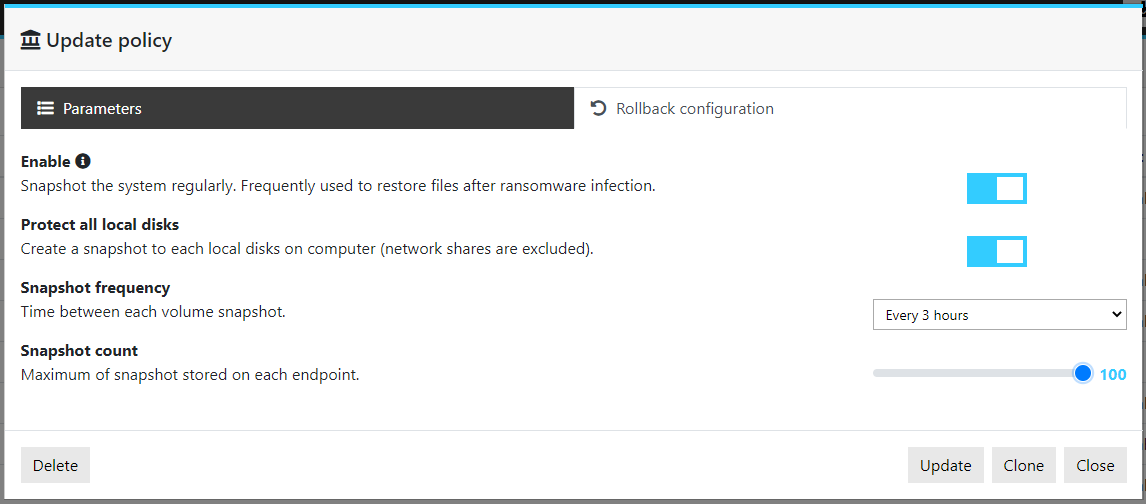
The snapshot feature is powered by the native Microsoft’s Windows Volume Shadow Copy technology (VSS). The rollback configuration of the policy allows to quickly set up the snapshot service to ensure a good snapshot configuration that fits your needs.
The first option allows to enable or disable the rollback feature, if it’s not enabled, no snapshot will be performed.
The second option allows you to snapshot all available local disks. Network shares are not snapshoted, the server hosting the data should manage the snapshot of the data in this case.
The snapshot frequency and the snapshot count can be modified in order to fit specific needs.
This feature is also compatible with third party application that already use the VSS service, the rollback parameter can be set to disable in this case. The rollback will use the existing snapshots even if they are not created by our rollback policy.
Rollback your data and Remediate after an incident like Hakbit ransomware
The goal of the feature is to restore the data and make the system to a normal state as quickly as possible when a data compromise occurs.
That’s why on each event and notification it is possible to request a rollback, this will automatically create some remote actions to operate on the target endpoint.
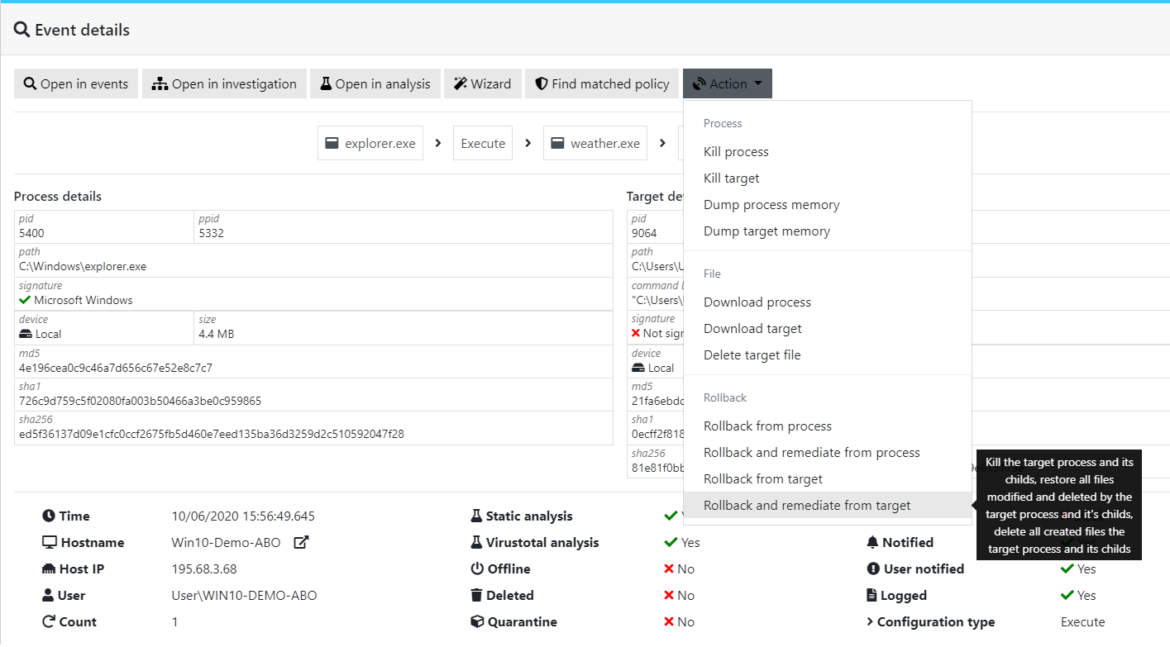
In order to ensure a complete cleanup and restoration of the system, multiple remote actions will be created :
- Isolation : the endpoint will be isolated and all network communication will be cut at a kernel level (except the access to the console) ;
- Kill : this action will kill the source process of the action, and follow all children created by this process to stop the malicious activity on the system ;
- Rollback & remediate : this action will retrieve affected data (modified, deleted or renamed) by the listed processes, and restore them to the date of the first execution of the main process ;
- Disable isolation : the network activity is back to normal and the computer can again be used.
In the following video, the ransomware hakbit is executed, and encrypt the user’s personal data. The EDR is set to detection mode to allow the malware to access the data, otherwise it would be blocked, and the malware would not be executed thanks to the analysis engine. Then a rollback is requested to restore affected data. The malicious file is also deleted thanks to the remediation option.
The preconfigured remote action can be customized, and some new ones can be added depending on specific needs to go deeper in the investigation, like retrieve Windows events, or dump the malicious process memory.
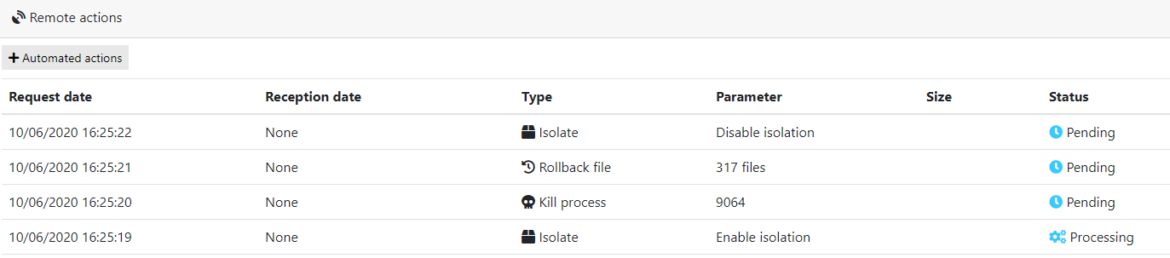
Each action will be executed step by step, and the system will be ready after few seconds of background actions on the machine. And this is how our rollback and remediation features are used against Hakbit or any otger ransomware.
Written by: Antoine Botte
Tagged as: rançongiciel, rollback.
Previous post
Malware Sébastien Guisnet
Corona-Malware la nouvelle tendance pour voler vos données
Similar posts


Don’t miss our insights
-
Articles récents
- Nucleon Security joins the Microsoft Virus Initiative to strengthen endpoint protection.
- Nucleon Security achieves an AAA score in the latest evaluation conducted by WestCoast Labs!
- Quels sont les enjeux stratégiques de la souveraineté en matière de cybersécurité ?
- Qu'est-ce que le Zero-Trust multicouche et comment il peut aider votre organisation
- Nucleon Security Vs Venus Ransomware
Catégories
Search in the site
Most popular

Copyright 2023 Nucleon Security